
Information requirements for digitisation in the health sector - Oqotech
Good practices in data integrity management are composed of controls provided by the computerized systems, the process equipment, the procedures implemented in the organization and the verification of the behavior finally obtained in the affected processes.


The computerization of critical business processes is becoming increasingly important for companies in the health, pharmaceutical, cosmetic and food sectors. The technological changes that have taken place in recent years, with an ever-increasing demand for digitized processes and rigorous real-time information, together with regulatory requirements, are turning the computerization of processes and the validation of computerized systems into strategic and necessary actions for any company.
The use of computerized systems can facilitate rapid access to information and can also be a way for health workers and patients to report data. The systems can also be used as tools in the management of industrial processes.
In this environment, the integrity of the data generated, processed, represented or stored in these systems is of vital importance. Throughout this article we will identify and detail the requirements applicable to information management in a computerized context within the scope of health-related sectors.
ALCOA+ rule requirements
The main regulatory expectation of data integrity compliance is centralised in the ALCOA+ rule. Initially, each letter of the word ALCOA represented a requirement that the information had to meet. Later, the requirements were expanded by adding the + symbol to the word ALCOA.
Data integrity applies to all critical information in the organization and therefore to the entire quality system. Being within its scope the quality system documents, computerized systems and process equipment. This implies standardization throughout the organization, establishing common and independent criteria of the format or medium of the data and its origin.
The requirements of the ALCOA+ rule are discussed below. The application of some requirements is aimed at the administrators of computerised systems, the characteristics of the computerised systems themselves and/or the verifications of the final behaviour of the process. Therefore, their application will have both a technical and procedural part of the system.
Attributable
The requirements for system administrators are as follows:
- User management. The coding of the users generated must allow the person to be uniquely identified.
- Management of security permits. Per workstation, avoiding the design of security profiles per user. The definition of profiles consists of assigning access to functionalities to qualified users.
- User access control and account blocking after several unsuccessful access attempts.
- Password management policy. Definition of complexity, renewal and periodic change.
Los requisitos para los sistemas informatizados son los siguientes:
- En el registro de las tareas reguladas debe quedar identificada la persona o sistema que genera el dato.
- En el registro de las tareas reguladas debe quedar identificada la persona o sistema que realiza la actividad que genera o modifica datos.
- En el audit trail debe quedar registro del alta, baja o modificación de los usuarios, perfiles de seguridad y contraseñas.
Legible
System requirements:
- The necessary data and metadata should be recorded in the register of regulated tasks.
- Both the original data and subsequent changes will be available.
- In the audit trail record of the regulated tasks, the necessary data and metadata must be recorded: date/time, user, affected entity, new value, old value and reason for change (for changes and deletions).
Being metadata the information that describes the attributes of the data, providing context and meaning and without which the data loses value and we cannot ensure its integrity.
Being audit trail the secure electronic record that allows the reconstruction of events related to the creation, modification or deletion of electronic records. It affects the system configuration, the process management itself and the generated records.
Contemporaneous
System requirements:
- Recorded and displayed at the time the activity is performed.
- Organization-managed date and time use, with no modification option for end users.
Requirements for users:
- Recorded and displayed at the time the activity is performed, without the use of intermediate supports.
- Organization-administered date and time use, in case the date and time is entered manually The date and time of data recording must always be recorded, regardless of when the data was obtained.
Requirements for developers and service providers:
- If the process consists of several steps, the result must be recorded at each step. In the event of an error, there will be no loss of partial data.
Original
The original record can be described as the first capture of information, whether recorded on paper or electronically. It preserves its content or meaning and nature.
Requirements for users:
- Registered at the time the activity is performed directly on the authorized media. Without the use of unauthorised intermediate media.
- The first reading, measurement or calculated result must be recorded.
- In case the user makes a mistake in recording the data, the original data and the modified data must be kept.
- Users should not have unauthorized copies of documents or forms at their disposal. All documents or forms must have a unique identifier.
- The design of the paper form should have sufficient space for corrections. In the case of an electronic record, the option of modification must be enabled for authorized users, and the original and new value must be recorded, as well as the reason for the change, as discussed in the requirements of the audit trail.
- Reviewers should be sure to review the original records. In the case of dynamic data, this should be done on the electronic data.
Exactly
- Precise data that will allow the total reconstruction of the activities that have led to the generation of the same. The precision of the record must be in accordance with the data obtained and the precision required for the process to be managed.
- Training for users to register data and use computerized systems.
- Maintenance and calibration of equipment carried out in accordance with approved procedures in the appropriate measuring range.
Complete
- All relevant data and metadata, including any repetition or modification, are considered complete data.
- When multiple results are generated, the user must ensure that all results are recorded correctly.
- The user in the paper record or in the use of computerised systems must follow a clearly defined procedure to invalidate a record. In no case should the original record be destroyed, but rather preserved as part of the complete data.
- Data can only be deleted after the archiving time and following the established procedure.
Consistent
- Prior to reviewing the conformity of critical data according to the technical specifications, the reliability of the data must be evaluated. This may involve reviewing the audit trail and metadata, verifying operational sequences, or verifying original data.
Enduring
- The data must be permanently recorded and maintained for the declared retention period. Procedures should confirm that archived data, including relevant metadata, are available and human readable.
- In the case of paper records, once the records have been completed, a procedure should be established for handing them over to a responsible person who will manage their safe storage throughout the declared archiving time.
- In the case of electronic records, a backup policy must be generated that identifies the data sources, the record’s place of origin, the type of backup and the destination of the backup (avoiding the storage of GxP data on the computers or PCs where the data originated). As well as determine the periodicity of the verification of the correct restoration of the data.
Available
- It must be ensured that GxP data that are in archiving period are available to authorized personnel of the organization and the competent authorities.
- The accessibility and readability of the data must be checked if relevant changes are made to the system (hardware or software), then the ability to retrieve the data must be guaranteed and checked.
Complete knowledge of the organization and risk-based control
The impact of incidents on data recording and integrity can be very significant in regulated industries. If it affects the product it can lead to non-conformities and sanctions. These deviations can have an economic impact.
Applying risk-based controls is a necessary strategy taking into account the impact on patient safety, product quality and data integrity. For the design of risk management (identification, evaluation, management and monitoring) it is advisable to take into account the methodology described by ICH Q9.
Requirements for the application of risk management:
- Complete knowledge and understanding of critical business processes.
- Identifying the operational scope of the computerized systems present in the organization.
- Identifying the design of the organization’s IT infrastructure: data processing center, physical and logical securities, servers, hardware and software, networks, communications and securities.
- Policy of maintenance of computerized systems.
- Subcontracted activities. Knowing the quality system of the technological service providers, establishing agreements that determine the requested activity and auditing them periodically to monitor compliance with the agreements.
- Complete knowledge and understanding of information flow.
- Identifying the organization’s users present in each process, taking into account their training.
Knowledge and control of information flow
Data management must be considered as a process in itself. It must focus on the entire data life cycle. Figure 1 identifies the main phases of the data life cycle and the critical points to be monitored in each of them.
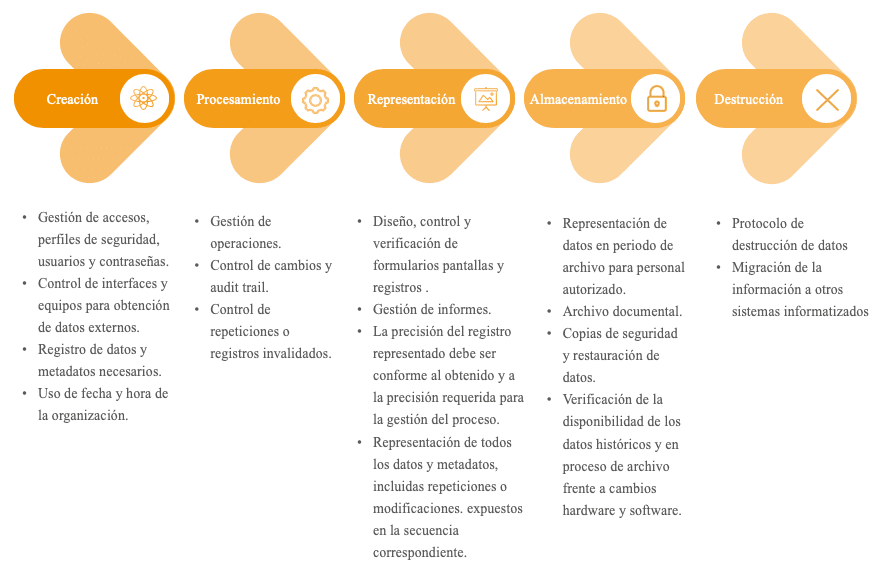

Verification of the controls applied and maintenance of the control status
It is necessary to establish mechanisms to verify the information management behaviour finally obtained in the affected processes, as well as procedures to maintain the control status. The main maintenance tasks are identified below:
- Inventory of computerized systems, process equipment and information flows.
- Risk analysis to establish priorities in the validation of computerized systems.
- Validation of computerized systems.
- Physical and logical security procedures.
- Management of users, security profiles and passwords.
- Training plan.
- Electronic signatures.
- Data backup and restoration policy.
- Control and review of the audit trail.
- Data archiving control.
- Equipment performance monitoring.
- Contingency and disaster recovery plan.
- Internal audit plan and service providers.
Conclusions
- We are in continuous increase of digitalization in the health sector. Computerized systems are used to provide real-time control of critical processes in organizations, for faster and easier access to information and as a registry for patients and doctors.
- The control and robustness of the data generated, processed, represented or stored in these systems is of vital importance.
- Existence of the ALCOA+ rule as a reference in the definition of requirements for data integrity compliance.
- A complete knowledge of the organization’s processes is required to provide the necessary controls to ensure data integrity. Risk-based controls must be established. The main risks are those provided by the process, technological and human.
- A complete knowledge of information flow is required to control the origin of critical information, data processing and data maintenance.
- It is necessary to periodically verify the behaviour of the information management finally obtained in the affected processes. As well as periodically reviewing the mitigation measures implemented such as validations, qualifications and management protocols.
In OQOTECH we help our clients to design and implement their strategy of equipment qualification in Data Integrity. Contact us and receive personalized advice for your company. We will solve all your doubts and comments.
Article originally published in Pharmatech’s magazine, issue 48, January-February 2020
Do you want to download this article? You can do it here








